Rakhoi TV – Link Xem Trực Tiếp Bóng Đá Không Giật Lag
Rakhoi làm say đắm tín đồ thể thao, nơi tận hưởng không khí sân cỏ tiện lợi và chất lượng. Sự đa dạng trong dịch vụ cung cấp cùng những tính năng hiện đại cho phép người hâm mộ thỏa đam mê ngay tại nhà trên mọi thiết bị. Điểm hẹn giải trí số 1 Việt Nam sẽ mang lại những lợi ích gì, mời bạn đọc cùng rakhoi tv khui màn bí mật dưới bài viết.
Tổng quan về trang thể thao Rakhoi
Rakhoi là một trang web thể thao với nhiều nội dung hấp dẫn và đa dạng bậc nhất hiện nay. Trang web với tiềm lực kinh tế mạnh dành tâm huyết cung cấp dịch vụ trực tiếp bóng đá, cho phép người dùng xem các trận đấu hàng đầu trên toàn thế giới. Với chất lượng hình ảnh sắc nét và link mới mỗi ngày, bạn có thể dễ dàng theo dõi các trận đấu yêu thích của mình.
Bạn có thể xem lại những khoảnh khắc đáng nhớ và những pha bóng đẹp từ các trận đấu quan trọng. Chỉ mới ra mắt thị trường thời gian gần đây nhưng rất được ưa chuộng bởi tính linh hoạt, độ chính xác cao và nhiều tính năng hiện đại. Bạn có thể cập nhật thông tin mới nhất về bóng đá và các môn thể thao khác chỉ qua một vài thao tác tìm kiếm cơ bản.
Đặc biệt trang Rakhoitv cung cấp các số liệu thống kê và thông tin chi tiết về các trận đấu, câu lạc bộ và cầu thủ. Bạn có thể tìm hiểu về thành tích, phong độ và các chỉ số quan trọng trong thể thao. Tự hào gây dựng được một cộng đồng người yêu thể thao đông đảo và nhiệt huyết. Bạn có thể tham gia vào các diễn đàn, bình luận, chia sẻ ý kiến và trò chuyện với những người cùng đam mê.

Thế mạnh vượt trội của sân chơi số 1 – Rakhoi
Rakhoi được biến đến là sân chơi số 1 dành cho những người yêu thích bóng đá trực tiếp. Có nhiều ưu điểm và thế mạnh đáng chú ý được đúc kết lại sau quá trình hoạt động đầy nỗ lực làm nên thương hiệu vượt trội. Liên tục nhận được đánh giá cao từ phía người dùng về mặt chất lượng thông tin cũng, điểm danh nhanh một số mục nổi bật sau.
Trực tiếp hình ảnh sắc nét từ sân cỏ
Hiếm có một địa chỉ nào có khả năng cung cấp trực tiếp hình ảnh sắc nét từ sân cỏ như Rakhoi. Chỉn chu trong từng tính năng mang đến cho người xem trải nghiệm chân thực như đang ngồi trên khán đài sân vận động. Với chất lượng hình ảnh cao, bạn có thể thưởng thức mỗi pha bóng, mỗi cú sút và mỗi bàn thắng với sự rõ ràng và sống động.

Cung cấp link mới mỗi ngày
Trang web không chỉ vang danh năm châu về việc cung cấp truyền hình trực tiếp, mà còn cập nhật link mới mỗi ngày. Điều này đảm bảo rằng bạn luôn có cơ hội xem những trận đấu mới nhất và không bỏ lỡ khoảnh khắc sân cỏ đáng nhớ nào. Bên cạnh đó còn luôn đồng hành cùng bạn trong việc theo dõi các trận đấu hấp dẫn trên khắp thế giới.
Thân thiện với mọi thiết bị khi xem rakhoi tv
Nền tảng thể thao hiện đại nên được thiết kế để tương thích với mọi thiết bị, từ máy tính, laptop đến điện thoại thông minh. Bạn dễ dàng tận hưởng không khí sân cỏ mọi lúc, mọi nơi và trên mọi hệ điều hành chỉ cần đảm bảo đường truyền kết nối internet ổn định. Điều này mang lại sự tiện lợi và linh hoạt cho người dùng trong thời đại công nghệ hóa hiện nay.
Xem lại bất kỳ trận đấu nào
Ngoài việc cung cấp trực tiếp bóng đá, Rakhoi cũng cho phép người dùng xem lại bất kỳ thời điểm nào. Bạn có thể lưu video về thiết bị và mở ra xem lại những khoảnh khắc đáng nhớ, những pha bóng đẹp và các tình huống gay cấn trong trận đấu yêu thích. Điều này giúp bạn không bỏ lỡ bất kỳ chi tiết nào và tận hưởng trọn vẹn niềm đam mê trái bóng tròn riêng mình.
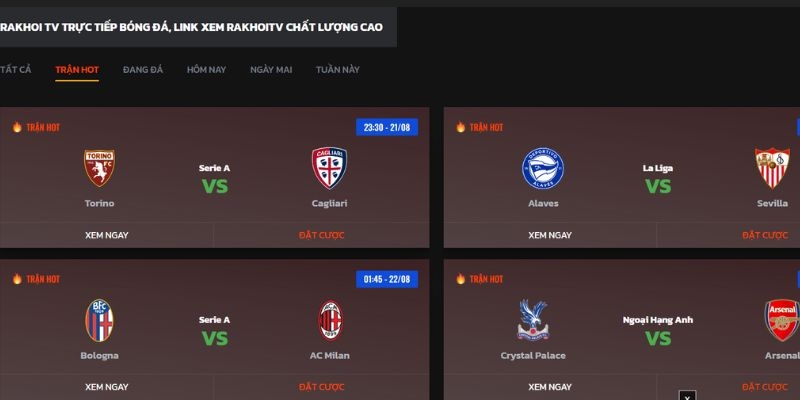
Hướng dẫn các bước tham gia Rakhoi cho newbie
Rakhoi đặc biệt phát triển giao diện tương thích với mọi nền tảng tạo sự thuận lợi cho người chơi tham gia. Anh em mới lần đầu có thể thực hiện theo các bước sau để nhanh chóng đáp ứng đam mê thể thao riêng mình:
- Bước 1: Chuẩn bị máy tính, điện thoại thông minh hoặc laptop được kết nối mạng và truy cập vào trình duyệt như Google, Cốc Cốc, Firefox, và cùng những trình duyệt khác.
- Bước 2: Nhập các từ khóa có liên quan đến trang web hoặc chuyên mục mà bạn muốn tìm kiếm.
- Bước 3: Khi website xuất hiện, truy cập vào đó và nhấp vào mục “Trang Chủ” trên thanh công cụ. Dựa vào giải đấu hoặc thời gian thi đấu, tìm trận đấu mà bạn muốn xem.
- Bước 4: Khi đã tìm được trận đấu, nhấp vào “Xem Ngay” và chọn đường link phù hợp với bạn để xem trực tiếp.
Rakhoi phát sóng hàng loạt giải đấu nổi tiếng
Rakhoi là một trong những website hàng đầu tại Việt Nam phát sóng trực tiếp tất cả các giải bóng đá hàng đầu. Tự hào có đầy đủ bản quyền phát sóng của những giải đấu hấp dẫn nhất trên thế giới và trong nước. Bạn dễ dàng tìm kiếm thông tin về giải mà mình yêu thích để bắt đầu trải nghiệm đáng nhớ mà không phải trả bất kỳ khoản phí nào, một số giải được tìm kiếm nhiều nhất phải kể đến:
- Cúp UEFA Champions League nổi tiếng.
- Giải Premier League bậc nhất nước Anh.
- Cúp Europa League danh giá.
- Giải Serie A với những màn biểu diễn đẳng cấp.
- Giải Liga cùng sự góp mặt của những câu lạc bộ nổi tiếng.
- Giải Bundesliga được xem là tinh hoa của bóng đá Đức.
- Giải Ligue 1 quy tụ đội bóng có tên tuổi trong khu vực.
- Giải V.League là linh hồn của người hâm mộ Việt Nam.
- Trực tiếp giải World Cup tìm ra ngôi vương toàn cầu.
Ngoài cập nhật thông tin cho các giải đấu có quy mô quốc tế trang web độc quyền song hành cùng Việt Nam. Các giải đấu mà đội tuyển Việt Nam tham gia như AFF Cup, U23 Châu Á, vòng loại World Cup hay cả Sea Games đều được update mỗi ngày. Tham gia vào trang web cũng là cách mà bạn gián tiếp cổ vũ cho các chàng trai, cô gái của nước ta vững bước trên con đường chinh phục bóng đá thế giới.

Dịch vụ thể thao chất lượng chỉ có tại Rakhoi
Rakhoi là sân chơi số 1 cho những người yêu bóng đá trực tiếp, với những ưu điểm vượt trội. Dễ dàng theo dõi trực tiếp hình ảnh sắc nét, cung cấp link mới mỗi ngày, thân thiện với mọi thiết bị và khả năng xem lại tiện ích. Trang web hiện đang đứng đầu thị trường về tính phong phú trong việc phát triển chuyên mục đáp ứng nhu cầu của người hâm mộ, điển hình như:
Video hightlight
Trang web cung cấp tất cả những video highlight cho các trận đấu và sự kiện thể thao quan trọng. Bạn có thể xem lại những khoảnh khắc đáng nhớ, những bàn thắng đẹp và các tình huống hấp dẫn ngay trên màn ảnh nhỏ. Video sẽ đi kèm với bài viết hoặc phần nhận định chuyên gia để người hâm mộ tiện theo dõi lại diễn biến trận đấu mà mình đã bỏ lỡ.
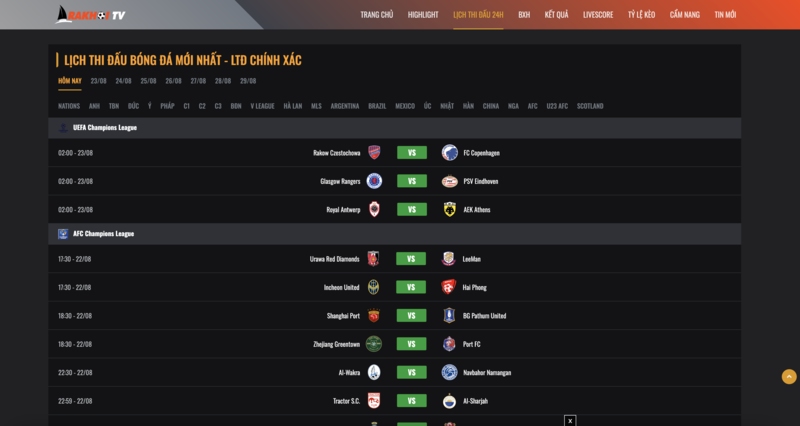
Lịch thi đấu bóng đá tại rakhoi tv
Trang web có riêng chuyên mục cập nhật lịch thi đấu bóng đá đầy đủ và chi tiết từ các giải đấu hàng đầu trên thế giới. Bạn có thể dễ dàng theo dõi thời gian và địa điểm diễn ra các trận đấu, giúp bạn không bỏ lỡ bất kỳ trận đấu nào. Tất cả đều quy về múi giờ Việt Nam, nhìn vào lịch bạn dễ dàng biết được thời điểm chính thức các cầu thủ sẽ ra sân thi đấu.

Bảng xếp hạng
Rakhoi sở hữu chuyên mục bảng xếp hạng với lượt người tìm kiếm tăng một cách chóng mặt mỗi ngày. Tổng hợp mới nhất mỗi ngày cho các giải đấu bóng đá hàng đầu về thứ hạng từ cao xuống thấp dẫn của các câu lạc bộ. Bạn có thể theo dõi vị trí của các đội bóng yêu thích và xem xét các cuộc đua tranh ngôi vô địch và suất dự các giải đấu quốc tế.
Tỷ lệ kèo tại rakhoi
Trang web cũng là điểm hẹn an toàn cho những tín đồ đam mê đặt cược, dự đoán kèo bóng đá. Hệ thống tỷ lệ kèo thể thao phong phú để bạn có thể đánh giá và so sánh các cơ hội cá cược của bản thân. Cập nhật thông tin kèo từ các nhà cái hàng đầu và sử dụng thông tin này để đưa ra quyết định cá cược thông minh kiếm thêm tiền thưởng gấp nhiều lần đầu tư.
Nhận định chuyên gia
Rakhoi cung cấp nhận định từ các chuyên gia thể thao, giúp bạn có cái nhìn sâu sắc và thông tin chính xác về các trận đấu. Đội ngũ hùng hậu với kiến thức rộng giúp bạn hiểu rõ hơn về tình hình của các đội bóng, phong độ của cầu thủ và các yếu tố quan trọng khác để đưa ra dự đoán chính xác. Bên cạnh đó còn có bình luận việc trực tiếp phân tích ngay trong diễn biến thực.
Kết quả bóng đá chuẩn xác
Chuyên mục kết quả bóng đá tại trang web rất được ưa chuộng, nơi bạn dễ dàng tổng hợp dữ kiện về giải đấu. Với tốc độ nhanh và chính xác từ các trận đấu trong nước và quốc tế là điểm mạnh tạo nên niềm tin đối với người hâm mộ. Bạn có thể cập nhật kết quả mới nhất và theo dõi thành tích của các đội bóng yêu thích của mình ngay sau tiếng còi trận đấu.
Dịch vụ thể thao tại Rakhoi hoàn toàn miễn phí
Toàn bộ dịch vụ mà trang thể thao Rakhoi đang cung cấp đến người dùng đều hoàn toàn miễn phí. Đây là lời khẳng định từ đội ngũ sáng lập, dù bạn tìm kiếm bất kỳ thông tin nào hay theo dõi video trực tiếp bóng đá của giải nào cũng rất dễ dàng. Hệ thống không yêu cầu trả phí cũng không cần đăng ký tài khoản lằng nhằng như địa chỉ khác.
Bạn thoải mái sống trọn đam mê riêng mình mỗi ngày trên bất kỳ thiết bị thông minh nào. Tuy nhiên có một số tính năng và tin tức độc quyền yêu cầu bạn phải có tài khoản thành viên nhưng không cần trả phí.

Kết luận
Với những thông tin được chúng tôi tổng hợp chi tiết cho bạn đọc kiến thức về một trang web thể thao hiện đại. Rakhoi đặt sự hài lòng và uy tín lên hàng đầu trong mọi dịch vụ cho anh em những giờ phút giải trí trọn vẹn niềm vui nhất. Bạn sẽ dễ dàng tìm kiếm cho mình lịch thi đấu, bảng xếp hạng hay hòa mình vào không khí cổ vũ cuồng nhiệt một cách dễ dàng.
